Just updated to Reinhardt.
You are currently browsing the monthly archive for February 2011.
I use Nagios to monitor my own servers (and clients’ servers and my employers’ servers, too) and I am giving the new Nagios V-Shell a test-run.
Why? I don’t actually care much about the fact that it’s written in PHP and generates valid XHTML. I am rather interested in the fact that it doesn’t use frames. My hopes are that the interface works nicely on BlackBerries and other smartphones. – Yes, there are frontends which were designed with small screens in mind, but they are either too focused on iPhones or Android with heavy use of JavaScript, or lack some important features such as the ability to acknowledge host or service states etc.
I have yet to test the V-Shell with multiple users, or other users than “nagiosadmin”… but this is the bottom line for today:
- Installation is very easy and straight forward
- V-Shell works fairly well on the BlackBerry – slow, but easy to use and intuitive; the views and controls are very close to the original Nagios Core web interface
- Two things weren’t working well in the beginning, but I managed to fix them…
Host icons
I use host icons. They’re mainly just pleasing to the eye in the HTML parts of the web interface, but very useful when you look at the status map. I maintain my own set of icon files in the Nagios Core web interface, but unfortunately the V-Shell doesn’t automatically link the host icons to that location (whereas it relies on the Core interface for service and host commands). My solution is:
- Remove the logos that shipped with V-Shell: rm -rf /usr/local/vshell/views/images/logos
- Create a symbolic link to the Core logos folder: cd /usr/local/vshell/views/images ; ln -s /usr/local/nagios/share/images/logos
- Append the following lines in the vshell_apache.conf files right before the line that says </Directory>
### for the logos Options +FollowSymLinks
NagiosGrapher
I still use the old NagiosGrapher. I know I should move to something newer, but I love my historical data and there are just so many other things on my todo-lists at the moment. The links to the graphs are not working from V-Shell, but this time the blame is not on V-Shell but on the NagiosGrapher. Anyway, I wanted a solution and here it is:
- Copy the NagiosGrapher CGIs (graphs.cgi, rrd2-graph.cgi, and rrd2-system.cgi) from your Nagios Core CGI folder to the V-Shell folder
- Append the following lines in the vshell_apache.conf files right before the line that says </Directory>
### for the nagios_grapher Options +ExecCGI AddHandler cgi-script cgi
I had always been a bit reluctant to enable the XML-RPC publishing feature on my blogs because this can be just an extra attack vector to a site. It is, however, required when you want to manage a WordPress blog using WordPress for BlackBerry. When your BlackBerry is connected to a corporate network using BlackBerry Enterprise Server, and your organization’s admins are OK with you using your mobile device and the corporate server to manage your blog (or if it’s a company website anyway), you can add the following lines to your .htaccess file to block any XML-RPC access to your blog which is not coming from your corporate server:
<Files xmlrpc.php> Order allow,deny allow from 198.51.100.27 </Files>
You will have to replace 198.51.100.27 with the IP address of your BlackBerry Enterprise Server.
Now you will also need to setup the WordPress app on your mobile device to use the BlackBerry Enterprise Server to connect to your blogs. In the app hit the BlackBerry key and click on “Setup”:
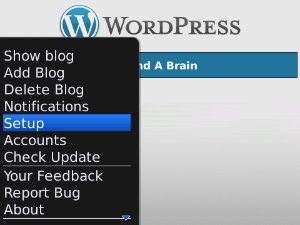
In the setup screen disable all other Connection Options and enable only “BlackBerry Enterprise Server” (this appears to be off by default):
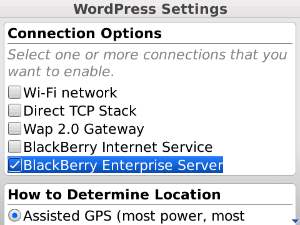
Now Apache will allow only your BlackBerry (well, and any other BlackBerry in the same organization) to connect to your blog.
A number of Unix/Linux tools, e.g. Subversion (svn) and wget, use OpenSSL when they access HTTPS sites. While I found updating the trusted CA store in curl (which does not use OpenSSL) very easy (I just downloaded their weekly CA bundle), OpenSSL isn’t as self-explaining. You may need this with older Linux distributions like openSUSE 10.3 running on “old” webservers, e.g. when you use svn to track changes of a web-application and keep the repository on encrypted webspace (highly recommended!) and the CA is not trusted in your distribution’s OpenSSL package. I use StartSSL Free Class 1 certificates for some of my private servers and their CA certificate is not included in many older distributions.
First you need to determine where OpenSSL keeps its files on your system. With the aforementioned openSUSE 10.3 this is
cd /etc/ssl/certs
Download your CA’s root certificate
wget http://www.startssl.com/certs/ca.pem -O startssl.pem
Determine the certificate’s hash
openssl x509 -noout -hash -in startssl.pem
For StartSSL this is “33815e15”. Now create a symlink to the certificate file with the hash as the filename and with the filename extension “.0”
ln -s startssl.pem 33815e15.0
Done.
If you prefer to know the backgrounds, read this OpenSSL Command-Line Howto!

Recent Comments